Configure the connection from Collibra DGC Cloud to Collibra Connect
The connection from Collibra DGC Cloud to Collibra Connect is optional. However, it is needed if any integration processes will be triggered by a Collibra DGC workflow.
As communication will be initiated by Collibra DGC Cloud, we recommend a reverse proxy server to receive the request from Collibra DGC Cloud, and then forward the request to the Collibra Connect server. This approach allows the Collibra Connect server to run behind the corporate network firewall, while the reverse proxy server can run in the DMZ of your organization.
In this article, we describe how to configure the connection from Collibra DGC Cloud to Collibra Connect.
Configure the gateway application for Collibra Connect
- Download the Collibra domain and gateway version 1.0.0 package (collibra-domain.zip) from the Collibra Downloads page.
- Only version 1.0.0 has the gateway application.
- Don't extract the ZIP file.
- Import the ZIP file in Anypoint Studio as Mule Deployable Archive.
The domain application and gateway application appear in Anypoint Studio. - In the Package Explorer pane, go to gateway → src/main/app.
- Double-click the gateway.properties file.
- Enter the Collibra DGC Cloud information that is shown in the following image as
dgc.config.*parameters.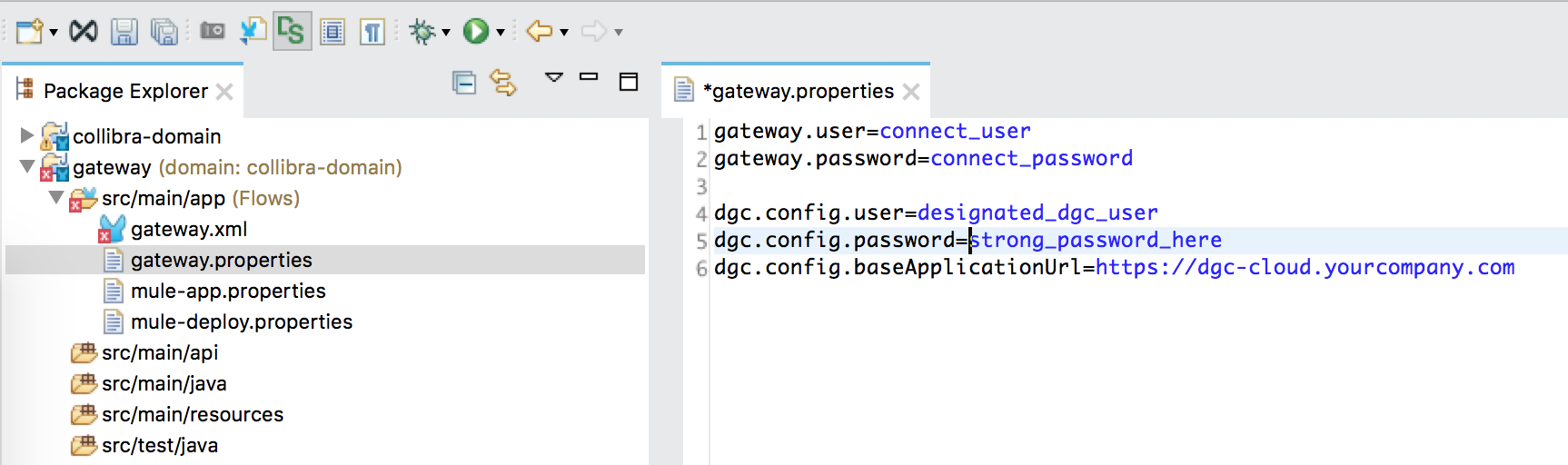
- Export collibra-domain as Mule Deployable Archive.
- Export gateway as Mule Deployable Archive.
- Install collibra-domain on your Mule ESB Server instance by copying the newly created ZIP file to MULE_HOME/domain.
The collibra-domain cannot be deployed via ARM or MMC.
- Install the gateway application on your Mule ESB Server instance:
Mule ESB Server managed by ARM or MMC
Mule ESB Server manually managed
- Log in to either ARM or MMC.
- Click the application deployment page.
- Deploy the ZIP file (Mule Deployable Archive) and follow the on-screen instructions.
Copy the ZIP file (Mule Deployable Archive) to the MULE_HOME/apps directory.
Configure the connection details
- Open Collibra Console with a user profile that has the SUPER role.
Collibra Console opens with the Infrastructure page. - Click the name of an environment to open its details.
- Click Configuration.
- Click Edit configuration.
- In the Collibra connect section, enter the Collibra Connect connection details:
Setting Description Base url The URL to the Collibra Connect gateway application. Username The username to connect to the Collibra Connect gateway.
The default value is connect_user.
Password The password to connect to the Collibra Connect gateway.
The default values is connect_password.
- The username and password must be the ones that you used to configure the gateway.
- The base URL
- If you are not using a reverse proxy server, enter the hostname or IP address of the Mule ESB Server runtime.
- If you are using a reverse proxy server, enter the hostname or IP address of the proxy server.
- Click the green Save all button.
Certificate configuration
If the gateway has a valid certificate instead of a self-signed certificate, then the following procedure is not required. However, it is likely that the gateway uses a self-signed certificate.
- Open Collibra Console with a user profile that has the SUPER role.
Collibra Console opens with the Infrastructure page. - Click the name of an environment to open its details.
- Click Configuration.
- Click Edit configuration.
- Go to the Security configuration section and then click SSL.
- Enter the SSL settings:
Setting Description Key store name The name of the key store file. The file is likely to be in the <collibra_data>/dgc/security folder. Key store password The password of the key store. Key store type The type of the key store file. For example, JKS or PKCS12. Trust store name The name of the trust store file. The file is likely to be in the <collibra_data>/dgc/security folder. Trust store password The password of the trust store. Trust store type The type of the trust store file. For example, JKS or PKCS12. - Click the green Save all button.
- Stop and start the environment again.